Featured Post
How To Find Private Key Cryptography
- Dapatkan link
- X
- Aplikasi Lainnya
Data encrypted with the public key can only be decrypted with the private key and data encrypted with the private key can. The private key is stored on your local machine.

Public Key Cryptosystems An Overview Sciencedirect Topics
To view the Private Key click the magnifier icon next to the relevant key in the Key column.

How to find private key cryptography. Each pair consists of a public key and a private key. On the new screen you should see. If you have followed the walkthrough you now have an authorized public key in place on your server.
Instead most asymmetric encryption implementations use hybrid encryption where a symmetric key is generated then this key is used to encrypt the files using symmetric encryption eg. D e 1 mod ϕ n This gives us d 23 which happens to be the same as e a coincidence. The other key is known as the private key.
By default the private key is generated in PKCS8 format and the public key is generated in X509 format. Effective security requires keeping the private key private. To use the keys you simply tell SSH where to find the private key when you open a connection.
He uses it and public key component n to decrypt the message. The public key can be openly distributed. Alice uses the encryption equation to encrypt the message.
Generate RSA Key Online Select RSA Key Size 515 bit 1024 bit 2048 bit 3072 bit 4096 bit. Dating back to the advent of cryptography private key cryptosystems were the first and continue to be the most common. Cd mod n m 25572753 mod 3233 42.
The Overflow Blog Observability is key to the future of software and your DevOps career. Browse other questions tagged cryptography aes ethereum private-key or ask your own question. The word key can be a bit misleading the key.
Public-key cryptography or asymmetric cryptography is a cryptographic system that uses pairs of keys. Private and Public Key cryptography derives its security from the Discrete Log Problem given the starting value and the end value its difficult to deduce the scalar Private Key. To calculate the private key we need to use the formula.
Jack receives the message. The key icon with the message Private key. Public key encryption or public key cryptography is a method of encrypting data with two different keys and making one of the keys the public key available for anyone to use.
When using private key cryptography both parties much each possess or at least exchange the private key. I have also computed ϕ n 24 and selected e such that gcd e ϕ n 1 by taking e 23. Private key encryption is the original type of encryption.
He has private key d 2753. Me mod n c 4217 mod 3233 2557 Now Alice has the message encrypted with Jacks public key. Use the appropriate method to get the private key such as GetRSAPrivateKey or use the CopyWithPrivateKey method to create a new instance with a private key.
The generation of such key pairs depends on cryptographic algorithms which are based on mathematical problems termed one-way functions. Log in To cPanel Servers with SSH Keys. On the cPanel home page click on SSLTLS Manager and then on the Private keys button.
Alice send the c ciphertext to Jack. AES then the symmetric key is encrypted using asymmetric encryption with the public key and stored along with the ciphertext. Click Domains your domain SSLTLS Certificates.
Youll see a page like the one shown below. How to retrieve a private key on different server platforms. Click on the File manager button from the cPanel home screen and.
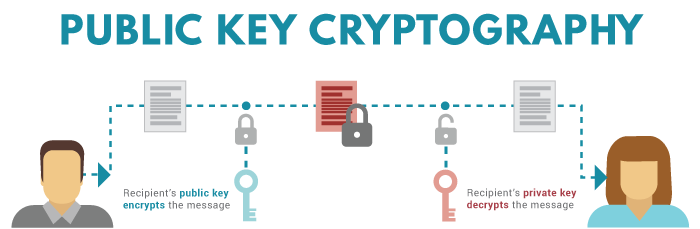
How To Generate Public And Private Keys For The Blockchain By Artiom Baloian Medium

What Is Public Key And Private Key Cryptography And How Does It Work

Public Key Cryptography Explained Sectigo Official

Private Key Cryptography Download Scientific Diagram
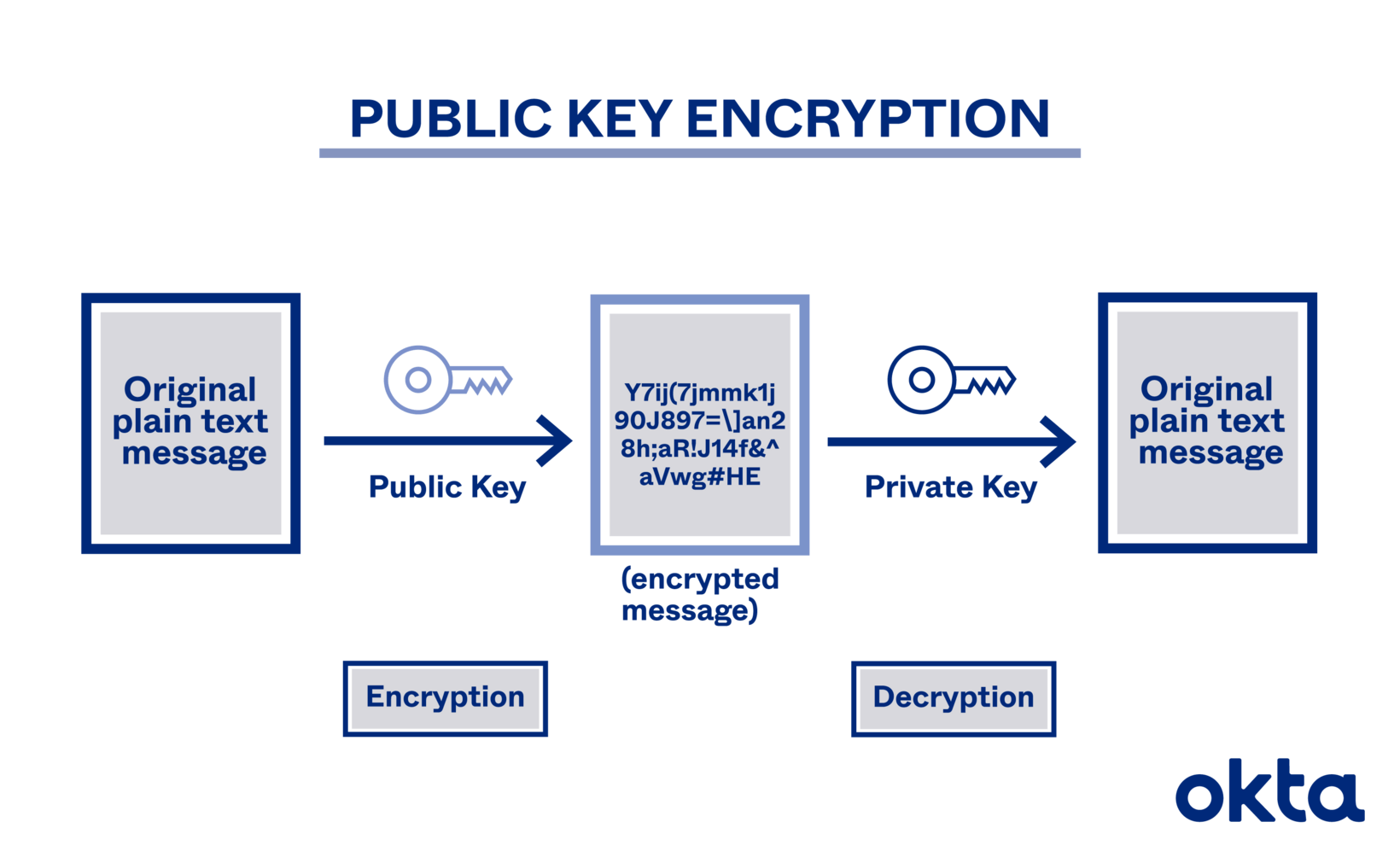
Public Key Encryption What Is Public Cryptography Okta

Public Key Cryptography Wikiwand
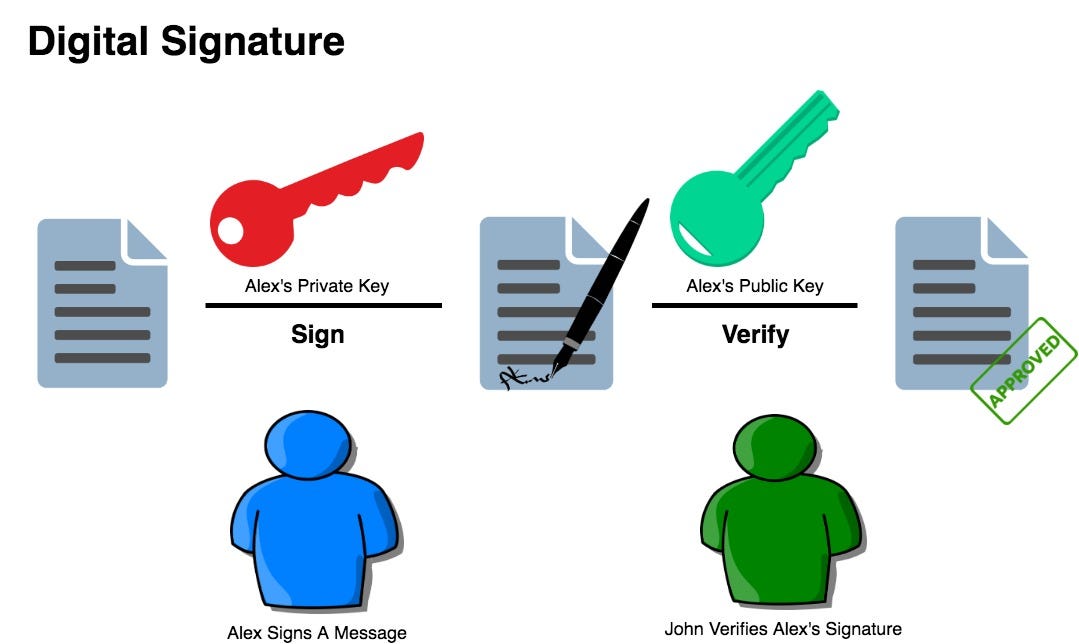
Blockchain Public Private Key Cryptography In A Nutshell By Demiro Massessi Coinmonks Medium

Public Key Vs Private Key How Do They Work Infosec Insights

Si110 Asymmetric Public Key Cryptography

Public And Private Encryption Keys Preveil
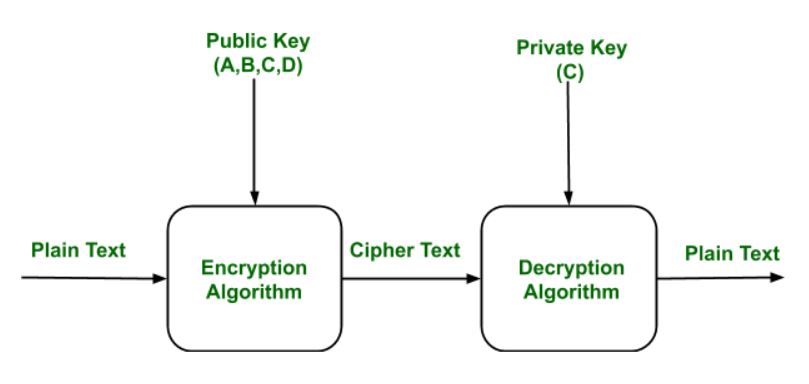
Public Key Encryption Geeksforgeeks

Public Key Cryptography And Digital Signatures By Anthony Albertorio Coinmonks Medium

Public Key Encryption Decryption Download Scientific Diagram

Private Key And Public Key With An Example Explained By Sslsecurity
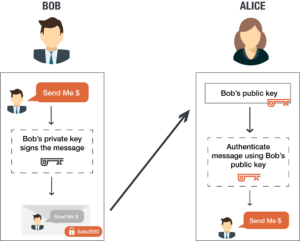
Public And Private Encryption Keys Preveil

Cryptography A Basic Public Key Example Wikibooks Open Books For An Open World
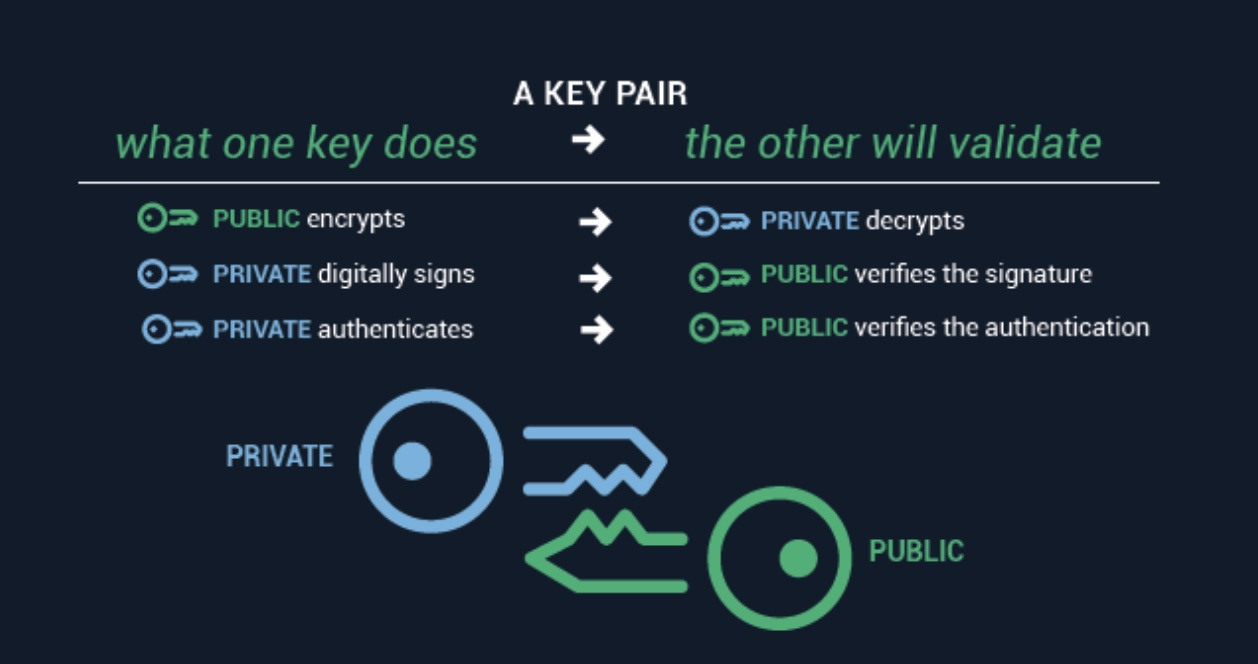
Public Key Cryptography Explained Sectigo Official
- Dapatkan link
- X
- Aplikasi Lainnya
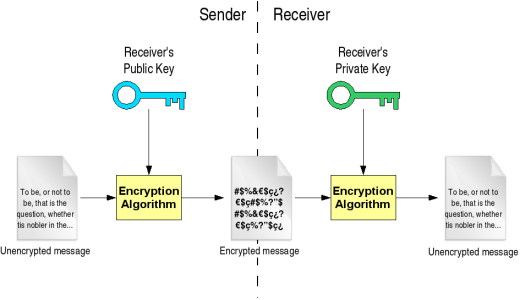

Komentar
Posting Komentar